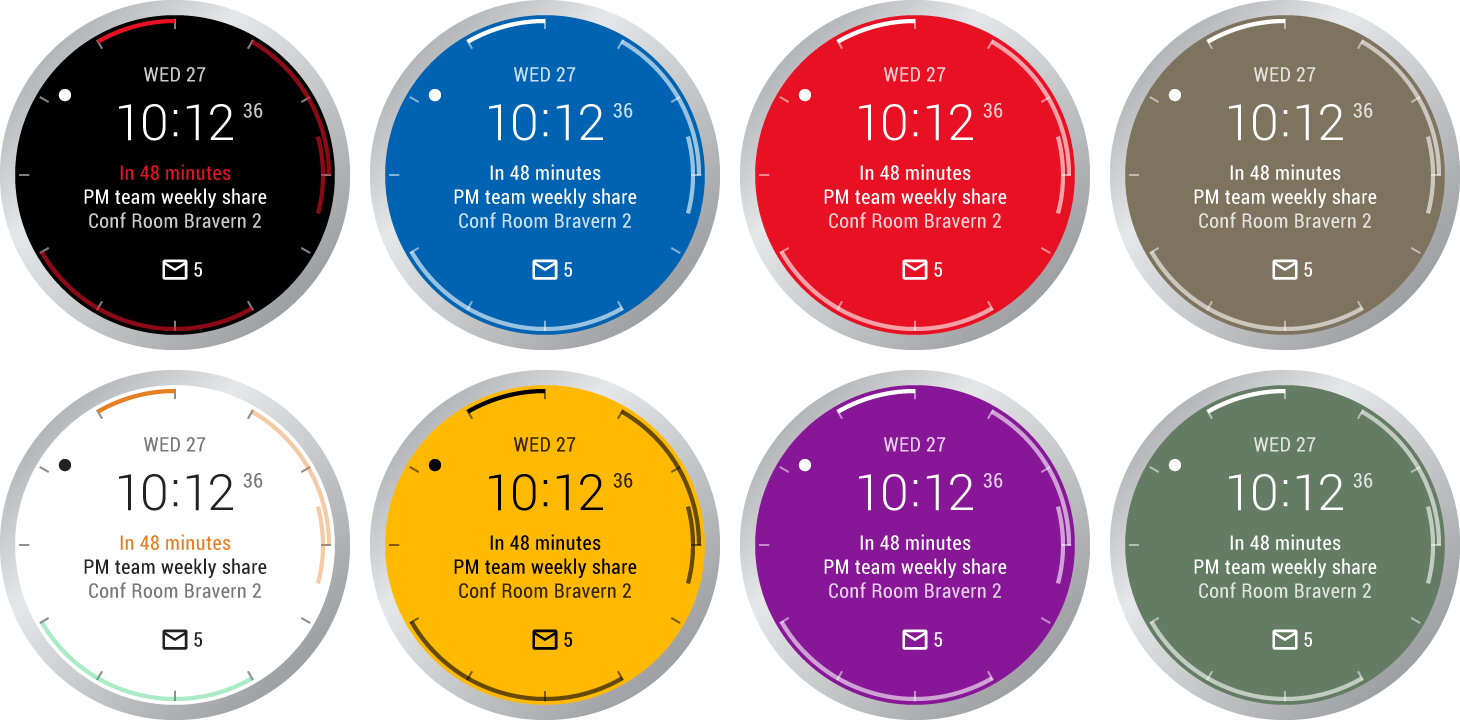
If I say Microsoft Outlook, what do you think? Personally, I think of the program I am forced to use at work and that has been around so long, it’s basically part of the digital furnitures now. So, if you’re Microsoft, how do you keep it current? Aside from the Android and ios app, Microsoft had released a somewhat limited version of the app on watchOS for the Apple watch. But now, they released on Android Wear and it looks amazing!

Basically, they designed the app to act like a watch face, giving you a glance at your emails, to do list and calendar, right on your wrist. After purchasing Sunrise, Acompli and Wunderlist, you knew it would be integrated at some time and we are starting to really see what Microsoft’s plan was… and we love it.
As a reminder, Acompli was an email app that basically became the outlook mobile app. Sunrise is a calendar app (which is stated to shutdown on August 31st) and Wunderlist is a to do list app that often was compared with the likes of Evernote and Google Keep. Now, all that is under one umbrella and easily noticeable on your wrist.
We are excited by everything Microsoft are doing nowadays and we can’t wait to see where they do from here. What about you? Let us know in the comments section below what you think of it and if you own a Android Wear, are you going to use it right away? We would be pleased to see some great comments! 😀