We all are addicted to social networking and other chatting and internet platforms but so few of us are aware of internet phishing so in this post we are gonna cover the topic: Phishing.
Before reading further you need to know what is phishing?
Phishing is all about acquiring sensitive information such as Username, Passwords , Credit Cards details, and sometimes indirectly money by showing yourselves as a trustworthy entity and it is typically carried out by e-mail spoofing or instant messaging and it often directs users to Enter their details at a fake websites whose look and feel are almost identical to the real one. phishing is an unending threat and risk is even larger in social networking sites such as Facebook , google+ and Twitter etc .
So, how do hackers take advantage of phishing using social media?
Hackers could create a clone of a website and tell you to enter personal information,which is then e-mailed to them and they mainly do this to Affect the Users and a Company, they take advantage of the trust that you have for a site.
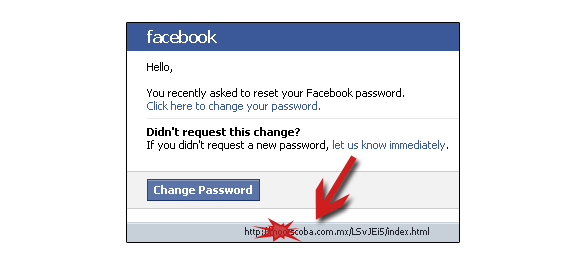
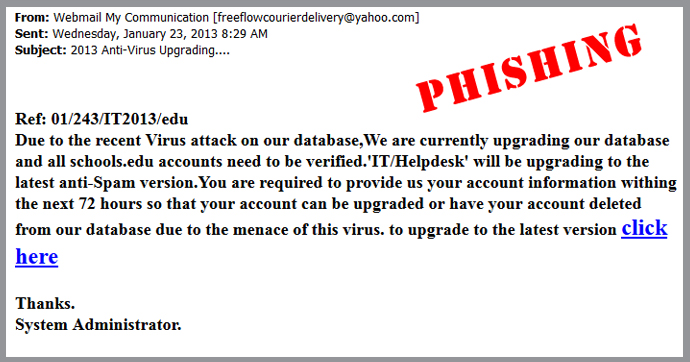
Not only is phishing done by websites but also with many common gadgets which we use in our everyday life.
PHONES
Not all phishing attacks require a website. Sometimes people receive a messages that fools the user by claiming to be from a bank, asking the user to dial a phone number regarding the problems in their bank accounts and once that phone number is dialed it prompts the user to tell their account numbers and PIN. This type of Phishing is commonly called Vishing ( Voice Phishing). Sometimes attackers use fake caller ID data to give themselves the appearance that the call is from a trusted organization.
number regarding the problems in their bank accounts and once that phone number is dialed it prompts the user to tell their account numbers and PIN. This type of Phishing is commonly called Vishing ( Voice Phishing). Sometimes attackers use fake caller ID data to give themselves the appearance that the call is from a trusted organization.
ALSO: (Off-Topic) Click here if you want to check Pan Card status
Damage caused by phishing
“It is estimated that between May 2004 and May 2005, approximately 1.2 million computer users in the United States suffered losses caused by phishing, totaling approximately US$929 million.”
users in the United States suffered losses caused by phishing, totaling approximately US$929 million.”
How to know that you are on a phishing site ?
Check the Web address. Just because the address looks OK, don’t assume you’re on a legitimate site. Look in your browser’s URL bar for these signs that you may be on a phishing site:
- Incorrect company name
 . Often the web address of a phishing site looks correct but actually contains a common misspelling of the company name or a character or symbol before or after the company name. Look for tricks such as substituting the number “1” for the letter “l” in a Web address (for example, www.paypa1.com instead of www.paypal.com).
. Often the web address of a phishing site looks correct but actually contains a common misspelling of the company name or a character or symbol before or after the company name. Look for tricks such as substituting the number “1” for the letter “l” in a Web address (for example, www.paypa1.com instead of www.paypal.com). - “http://” at the start of the address on Yahoo sign-in pages. A legitimate Yahoo sign-in page address starts with “https://” ― the letter “s” must be included. So check the website address for any Yahoo sign-in page.
- A missing forward slash. To verify that you’re on a legitimate Yahoo site, make sure a forward slash ( / ) appears after “yahoo.com” in the URL bar, for example, “https://www.yahoo.com” is a fake website address.
Be leery of pop-ups. Be careful if you’re sent to a website that immediately displays a pop-up window asking you to enter your username and password. Phishing scams may direct you to a legitimate website and then use a pop-up to gain your account information.
asking you to enter your username and password. Phishing scams may direct you to a legitimate website and then use a pop-up to gain your account information.
Give a fake password. If you are not sure if a site is authentic, don’t use your real password to sign in. If you enter a fake password and appear to be signed in, you’re likely on a phishing site. Do not enter any more information; close your browser. Keep in mind, though, that some phishing sites automatically display an error message regardless of the password you enter. So, just because your fake password is rejected, don’t assume the site is legitimate.
Use a Web browser with anti phishing detection. Internet Explorer, Mozilla Firefox, Web browsers have free add-on (or “plug-ins”) that can help you detect phishing sites.
Be wary of other methods to identify a legitimate site. Some methods used to indicate a safe site can’t always be trusted. A small unbroken key or locked padlock at the left of the URL bar of your browser is not a reliable indicator of a legitimate website. Just because there’s a key or lock and the security certificate looks authentic, don’t assume the 10 Best torrent sites is legitimate.
A little skepticism while browsing can go a long way in keeping you safe and in this day and age where we just can’t stay disconnected, staying safe while being connected is more important than ever before.
than ever before.


Its very strange to say about this phisShing We shoul be awared about this trapiing nd we mst care about this