Lead Image: South Korean researchers have discovered that reactive astrocytes, rather than amyloid-beta plaques, may be the main cause of Alzheimer’s disease. The team developed a new imaging technique using PET scans with radioactive acetate and glucose probes to visualize the interaction between astrocytes and neurons in Alzheimer’s patients. The researchers found that acetate, previously thought to be an energy source for astrocytes, can promote reactive astrogliosis and suppress neuronal metabolism. This breakthrough could lead to a new method for early diagnosis of Alzheimer’s disease and identify MCT1, an astrocyte-specific acetate transport, as a potential therapeutic target.
PET imaging of reactive astrocyte-neuron interaction reveals new insights into Alzheimer’s disease pathology, offering a potential breakthrough in diagnosis and treatment.
Recently, a team of South Korean scientists led by Director C. Justin LEE of the Center for Cognition and Sociality within the Institute for Basic Science made a new discovery that can revolutionize both the diagnosis and treatment of Alzheimer’s Disease. The group demonstrated a mechanism where the astrocytes in the brain uptake elevated levels of acetates, which turns them into hazardous reactive astrocytes. They then went on further to develop a new imaging technique that takes advantage of this mechanism to directly observe the astrocyte-neuron interactions.
Alzheimer’s disease (AD), one of the major causes of dementia, is known to be associated with neuroinflammation in the brain. While traditional neuroscience has long believed that amyloid beta plaques is been the cause, treatments that target these plaques have had little success in treating or slowing the progression of Alzheimer’s disease.
On the other hand, Director C. Justin LEE has been a proponent of a novel theory that reactive astrocytes are the real culprit behind Alzheimer’s disease. Reactive astrogliosis, a hallmark of neuroinflammation in AD, often precedes neuronal degeneration or death.
Lee’s research team previously reported that reactive astrocytes and the monoamine oxidase B (MAO-B) enzyme within these cells can be utilized as therapeutic targets for AD. Recently, they also confirmed the existence of a urea cycle in astrocytes and demonstrated that the activated urea cycle promotes dementia. However, despite the clinical importance of reactive astrocytes, brain neuroimaging probes that can observe and diagnose these cells at a clinical level have not yet been developed.
In this latest research, Lee’s team used positron emission tomography (PET) imaging with radioactive acetate and glucose probes (11C-acetate and 18F-FDG) to visualize the changes in neuronal metabolism in AD patients.
Dr. NAM Min-Ho, one of the first authors of this paper, stated, “This study demonstrates significant academic and clinical value by directly visualizing reactive astrocytes, which have recently been highlighted as a main cause of AD.”
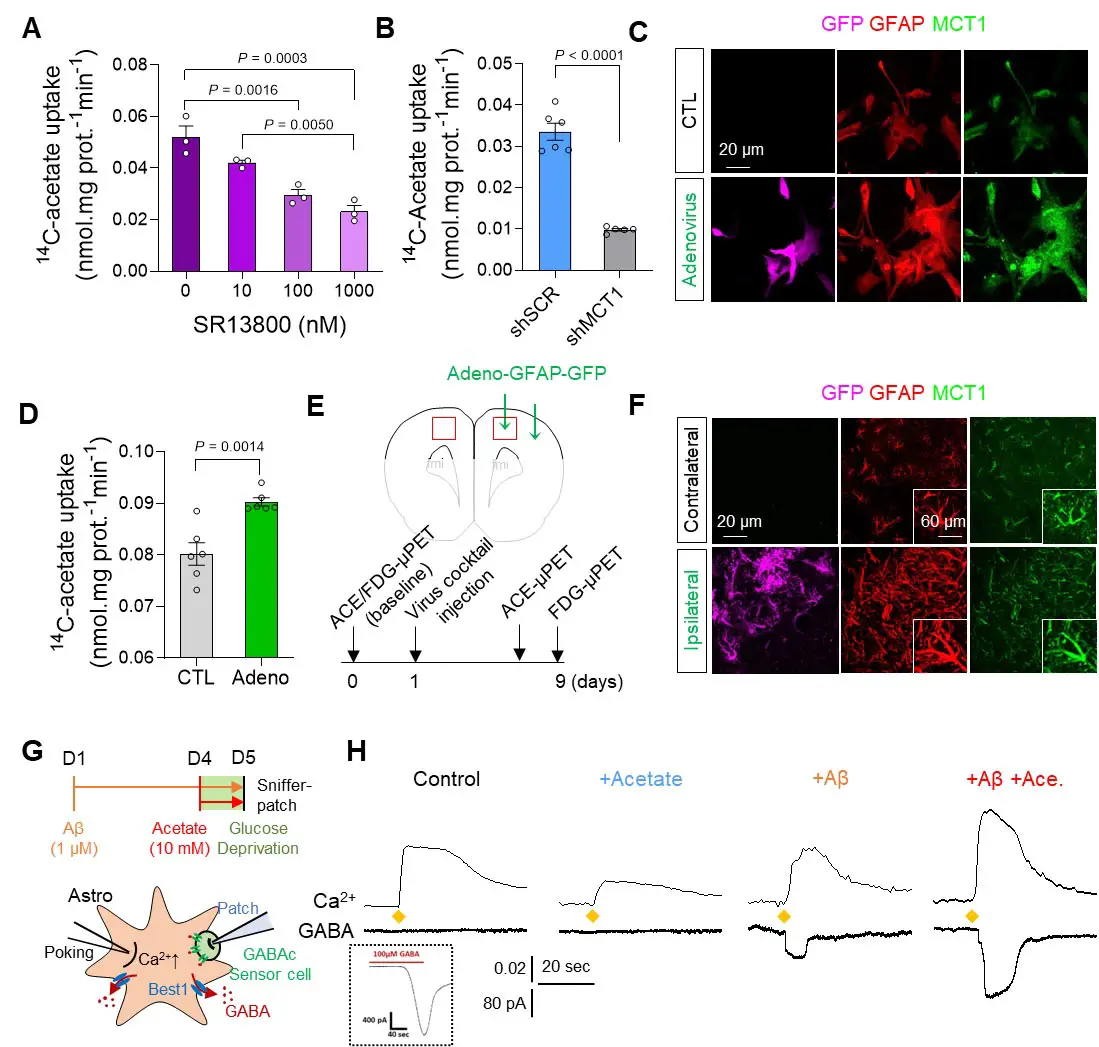
Furthermore, they demonstrated that acetate, the main component of vinegar, is responsible for promoting reactive astrogliosis, which induces putrescine and GABA production and leads to dementia. First, the researchers demonstrated that reactive astrocytes excessively uptake acetate through elevated monocarboxylate transporter-1 (MCT1) in rodent models of both reactive astrogliosis and AD (Figure 1A to 1F). It was discovered that the elevated acetate uptake is associated with reactive astrogliosis and boosts the aberrant astrocytic GABA synthesis when amyloid-beta, a well-known toxin protein in AD, is present (Figure 1G & 1H).
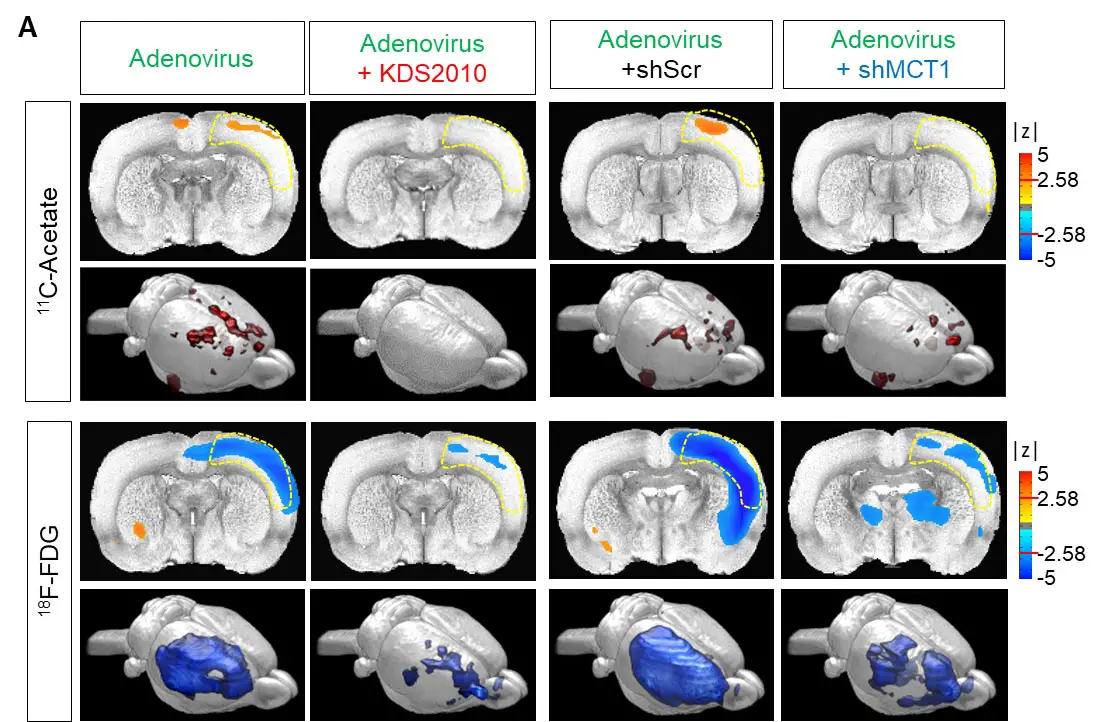
The researchers showed that PET imaging with 11C-acetate and 18F-FDG can be used to visualize the reactive astrocyte-induced acetate hypermetabolism and associated neuronal glucose hypometabolism in the brains with neuroinflammation and AD (Figure 2A). Moreover, when the researchers inhibited reactive astrogliosis and astrocytic MCT1 expression in the AD mouse model, they were able to reverse these metabolic alterations.
Dr. YUN Mijin commented, “Reactive astrocytes showed metabolic abnormalities that excessively uptake acetate compared to normal state. We found that the acetate plays an important role in promoting astrocytic inflammatory responses.”
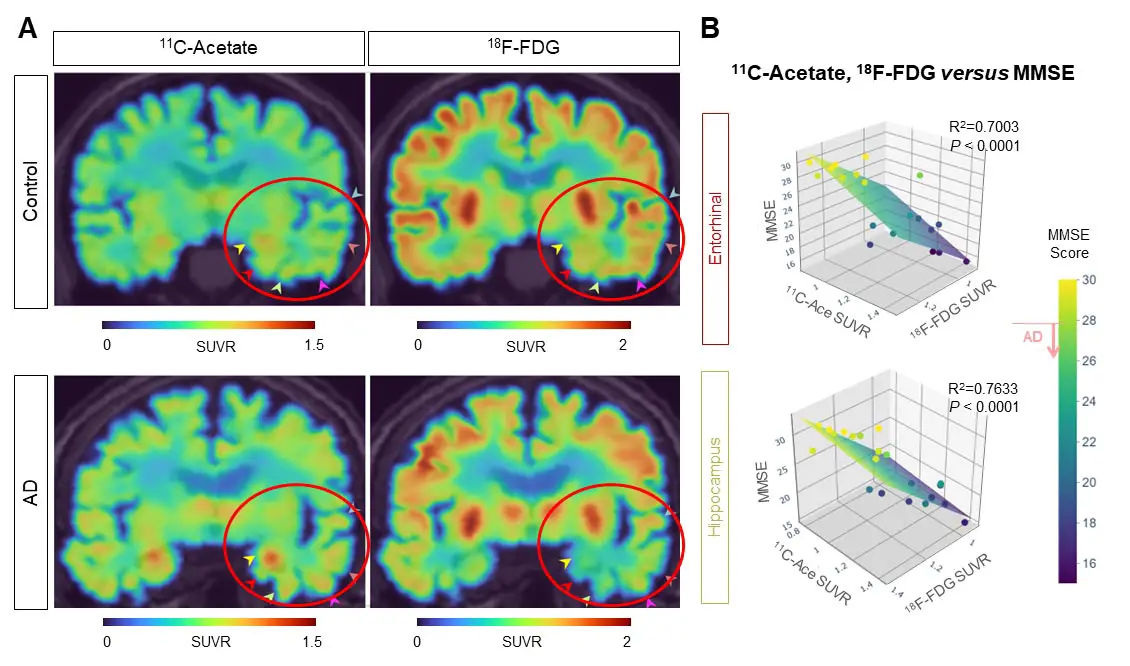
By using this new imaging strategy, the group discovered that alterations in acetate and glucose metabolism were consistently observed in the AD mouse model and human AD patients (Figure 3A). They were able to confirm that a strong correlation exists between the patient’s cognitive function and the PET signals of both 11C-acetate and 18F-FDG (Figure 3B). These results suggest that acetate, previously considered an astrocyte-specific energy source, can facilitate reactive astrogliosis and contribute to the suppression of neuronal metabolism.
Dr. RYU Hoon remarked, “By demonstrating that acetate not only acts as an energy source for astrocytes but also facilitates reactive astrogliosis, we suggested a new mechanism that induces reactive astrogliosis in brain diseases.”
Until now, amyloid beta (Aβ) has been suspected as the main cause of AD, and thus they have been the main focus of most dementia research. Unfortunately, PET imaging targeting Aβ has had limitations in diagnosing patients, and drugs aimed at removing it as a target for AD treatment have all failed so far. However, this study offers us a new possibility of using 11C-acetate and 18F-FDG PET imaging for early diagnosis of AD. In addition, the newly discovered mechanism of reactive astrogliosis through acetate and MCT1 transporter suggests a new target for AD treatment.
Dr. C. Justin LEE stated, “We confirmed a significant recovery when inhibiting MCT1, astrocyte-specific acetate transport, in an AD animal model,” and added, “We expect MCT1 can be a new therapeutic target for AD.”
Reference: “Visualizing reactive astrocyte-neuron interaction in Alzheimer’s disease using 11C-acetate and 18F-FDG” by Min-Ho Nam, Hae Young Ko, Dongwoo Kim, Sangwon Lee, Yongmin Mason Park, Seung Jae Hyeon, Woojin Won, Jee-In Chung, Seon Yoo Kim, Han Hee Jo, Kyeong Taek Oh, Young-Eun Han, Gwan-Ho Lee, Yeon Ha Ju, Hyowon Lee, Hyunjin Kim, Jaejun Heo, Mridula Bhalla, Ki Jung Kim, Jea Kwon, Thor D. Stein, Mingyu Kong, Hyunbeom Lee, Seung Eun Lee, Soo-Jin Oh, Joong-Hyun Chun, Mi-Ae Park, Ki Duk Park, Hoon Ryu, Mijin Yun, C. Justin Lee., 16 April 2023, Brain.
DOI: 10.1093/brain/awad037